Stealthy social network (Twitter / Facebook) based pentest drop box

The best place to exchange a secret is amongst a crowd - unknown.
With the amount of traffic generated by social networks, what if you could camouflage the pentest drop box traffic?
Pentest drop box - a portable device that is plugged (or connected wirelessly) to the target network during pentests and can be controlled from a command and control (C&C) server to perform the following functions:
- Network monitoring / sniffing
- Scan /exploit other hosts in the network
- ARP / DNS poisoning for MiTM attacks
- Denial of service
Drop boxes can call C&C using a number of methods, not limited to:
- Reverse SSH (over OpenVPN)
- SSH over HTTP(s)
- DNS tunneling - here is a good write-up
- Route through TOR
- ICMP based shell
- Egress buster - try all outbound ports until you find an open port
- Use a 3G dongle so that the C&C commands don’t touch the target network
Most of the above methods will require a persistent connection (shell) with your C&C, increasing the chances of detection. Often your connection may get interrupted, so you may also need a re-connect mechanism.
So, how can you create an near perfect C&C mechanism?
It should blend with the rest of the network traffic and be asynchronous. Of course, encryption is a must.
Say hello to social media based drop boxes.. !!
I wrote a blog post earlier on using Facebook API for data exfiltration during Red team pentests. A similar method was used to create a C&C for the drop box here.
The advantage here is that it can be quite hard to distinguish the drop box C&C traffic from the legitimate social network traffic. The social network API calls offer HTTPS encryption, which is a huge advantage.
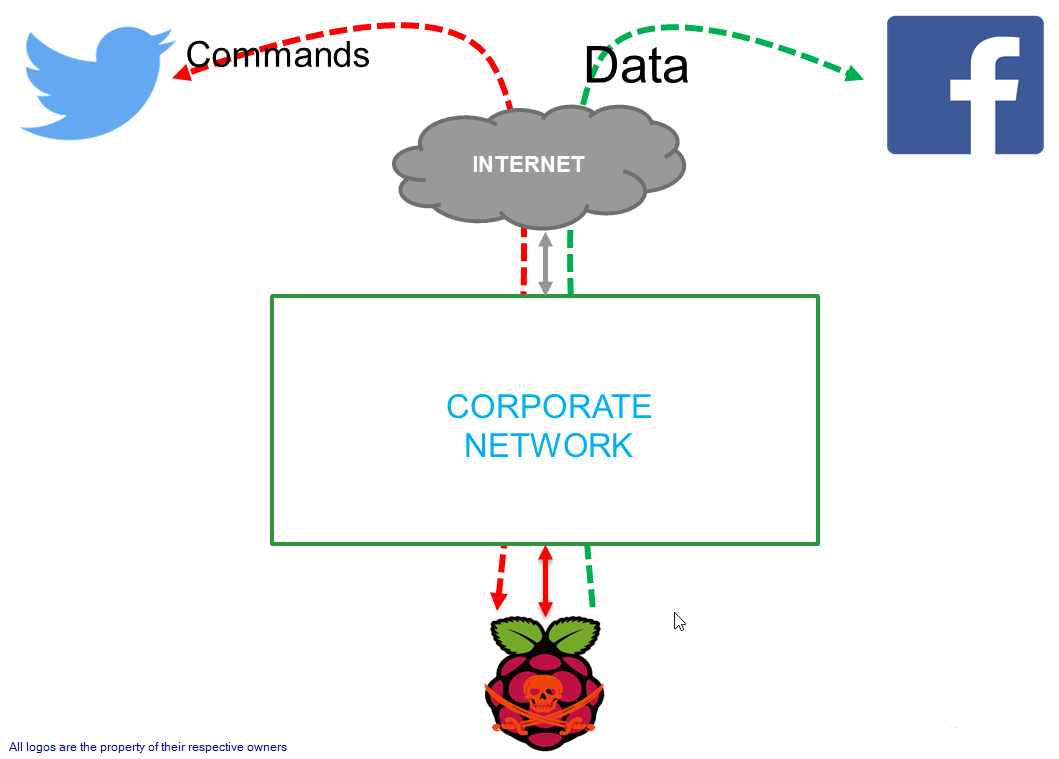
Design
Upstream - for receiving commands from C&C
Twitter - has a tweet limit of 140 characters, perfect for issuing commands to the drop box. The API calls uses HTTPS by default.
Downstream - for receiving the results of commands, data exfiltration
Facebook - has a post limit of 63,206 characters - which in most cases can be sufficient to receive command outputs like nmap scan results.
Stealth
To prevents mining of C&C tweets and posts made to Facebook, it is advisable to limit the privacy options.
Hardware
The pentester’s life has become a lot easier during physical pentests, thanks to the single board computers and the support they get. This gives a lot of freedom in terms of customizing the drop box in terms of software that needs to be on the box. Essentially, you can now build a drop box from scratch with only the tools you need. The low price tags are also an added advantage.
I’m a big fan of Raspberry Pi (RPi), so my drop box builds have been based on them till now. Black Hills Information Security had published a blog post on building your own drop box along with the a detailed comparison of single board computers. They have been doing some really cool research stuff and this is no exception. If you are planning to build a box on your own, I would highly recommend reading their blog post to start with.
Software
There is a Kali build for RPi available and it is possible to use their metapackages to customize for your engagement - web, Wi-Fi etc. If you want to keep it really light weight, you can also start with the Raspbian Lite and then customize for your needs.
Demos
For the sake of the demo, I will be running the scripts manually. During deployments, I simply start the script at boot and let it query for commands every minute or so.
During the demo, I will be showing how the commands are passed as tweets which are retrieved and executed by the drop box. The results of the command are then posted to Facebook page.
Demo video (YouTube link):
Mitigations
It will be hard to come up with a solution to completely mitigate this from a Blue team perspective. DNS and deep packet inspection would be the way to go.
Follow-up
Any suggestions / thoughts and mitigations are welcome.
Hope you find some use for this during pentests.
Cheers !!