
hotstar
OpenVPN on OPNSense -> NordVPN - Selective traffic routing
This post details how to configure a NordVPN OpenVPN client on OPNSense and selectively route client traffic over the tunnel.

vpn
This is a replica of the Surfshark VPN post from earlier, adapted for Proton VPN. Tested on OPNsense 24.7.10_2-amd64. Generate Proton VPN Wireguard configuration Login to Proton VPN and navigate to Downloads Select the options that you need Scroll down to the server location you need and

wireguard
I was trying to route traffic from selected clients over the Surfshark WireGuard tunnel using the official documentation here and ran into issues. Here is how I finally managed to set it up with help from Reddit threads [1] and YouTube [1]. Tested on OPNsense 24.1.10_3-amd64. Generate

nordvpn
💡This has not been tested in a while. Check NordVPN official page for connectivity options. Update (Nov/2020): Made a few modifications to make the script work again. This is going to be a quick tutorial (/self-reference) to set up Raspberry Pi as a VPN router for NordVPN. I ran

cloudflare
While using nginx-proxy from jwilder with Cloudflare, one of the common issues you run into is that the logs contain the Docker internal IP rather than the real external IP passed by Cloudflare. Note - During my tests, this only applies when nginx-proxy is run as two separate containers -

metasploit
If you have ever tried embedding EXEs in an existing PDF file using Metasploit, most likely you might have come across the error: [-] Sorry, I'm picky. Incompatible PDF structure: key not found: "Root". Please try a different PDF template. Details on the ‘Adobe PDF Embedded

raspberry pi
Wimonitor is a wonderful product from Hacker Arsenal that saves pentesters the hassle of having to configure VMs, carry compatible wireless cards that support monitor mode etc. and comes with a web interface to do the configurations. It gives you the flexibility to plug in the device into the Ethernet

virtualbox
This took me quite a bit of time to figure out, hopefully someone finds the steps useful. Many of the wireless cards that support monitor mode are all USB 2.0 devices - e.g. Alfa AWUS036NHA, TP-LINK TL-WN722N and run into problems while connecting to newer laptops that come

raspberry pi
MotionEyeOS is a wonderful project by Calin Crisan that converts your single board computer into a video surveillance system in a matter of minutes. It is supported on a number of devices and is well maintained with good community support. Now that the latest Raspberry Pi Zero version (W) comes

social media
Once you gain access to a system during pentest, you might want to retain access by means of a backdoor. The most trivial method is to use metsvc which ‘unfortunately’ is very well fingerprinted by anti-virus software. In this post, let us look at how to use a backdoor that

The best place to exchange a secret is amongst a crowd - unknown. With the amount of traffic generated by social networks, what if you could camouflage the pentest drop box traffic? Pentest drop box - a portable device that is plugged (or connected wirelessly) to the target network during

Question - In a controlled corporate environment with DLP solutions monitoring the HTTP and Email traffic, how would you perform data exfiltration during a Red Team Pentest ? ‘One’ of the answers would be to use social networking sites, let’s look at Facebook in this post. Data exfiltration using Facebook

💡This issue has been fixed on Windows 8+ as part of MS16-112 issued in September 2016. I haven’t checked this on a Windows 7 machine which isn’t listed on the Microsoft page. Basics The basic theory behind the attack is same as @mubix’s discovery - if you

In the previous post, a Raspberry Pi Zero was modified to capture hashes (or rather NTLMv2 responses from the client). Let’s see how hashcat can be used to crack these responses to obtain the user password. I will be using dictionary based cracking for this exercise on a Windows
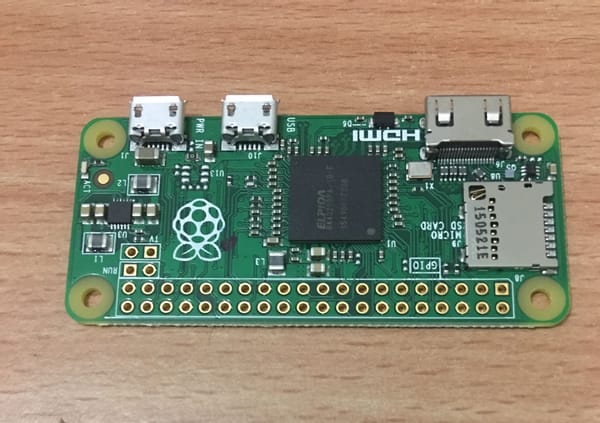
💡Update: CVE-2016-3302 / MS16-112 patch was released by Microsoft to fix the issue. Introduction This post is an extension to Rob Fuller’s (@mubix) work - https://room362.com/post/2016/snagging-creds-from-locked-machines/ to see how a Raspberry Pi Zero can be used for credential snagging. All credits go to @mubix for